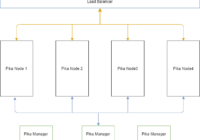
Docker build with multiarch
When building Docker images, you can specify the architecture using the –platform flag with the docker build command. This is particularly useful when working with multi-architecture builds or targeting platforms different from your host machine. Explanation –platform: Specifies the target platform for the build. The format is os/arch (e.g., linux/amd64, linux/arm64, etc.). -t: Sets the name and… Read More »