Implementation of API Authentication, Authorization, and Access Control
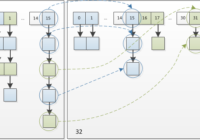
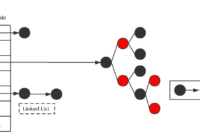
Overview If the API interface docked with the front-end is captured by a third party and maliciously tampered with the parameters, it may cause data leakage or even tamper with the data. I mainly focus on the three parts of timestamp, token, and signature to ensure the security of the API interface. 1. After the user successfully logs… Read More »